
This post essentially was going to be about how to enable ssh on the cisco router. But.. I realized that in many cases when I say to someone:
- You should stop using telnet while accessing your cisco device via public network (internet), because traffic is not encrypted and it is easy to sniff and see your passwords, your running config and anything you type and your router response. It is like having keylogger on your system. Use ssh instead, so traffic is encrypted and you are much safer.
That "someone" (you?) often says:
- Really? Oh.. probably it is not so easy to sniff, come on!
Because of this I will show how "safe" you are using telnet. The second reason is because I can see the analogy from martial arts (I hope you like it). Before you learn how to block/protect yourself, you need to know how to strike first!
Please take a look at Figure 1. We will telnet from Microsoft Windows "XP" to Router "R", sniff the telnet traffi using wireshark, decode and read.
Below are scary results:


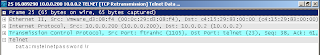
No way! You might say. As you can see if you use telnet someone can learn your passwords and your config, and if someone has bad day that time may wipe out your router config and reboot... You probably do not want to come to work and see this in the morning do you?
Let's fix it and enable ssh:
en
conf t
username cisco password cisco
aaa new-model
ip domain-name mydomain.com
cry key generate rsa
!
! --- use 2048 bit as a key length, and allow couple minutes for your router to generate key
!
line vty 0 4
!--- enable ssh service only
transport input ssh
end
wr
It will look like:
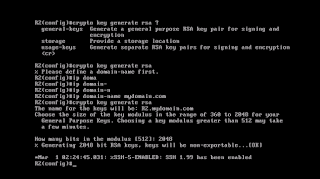
We are done, now we should use ssh client, from windows we will use putty. Take a look what can we sniff this time:


Try to guess my password now!
As we can see the security level has been improved a lot. It did not take too much effort either. I hope it will help to understand that telnet should be replaced by ssh usage, unless you do no care about security of your passwords or running config. It is possible if you are just using the router for quick and dirty testing or learning purposes.
Note: Please note that after you changed your connection type from telnet to ssh, you should change all passwords since someone could already sniff the current one.
Make sure your IOS support ssh using Ciso IOS advisor:
http://tools.cisco.com/ITDIT/ISTMAIN/servlet/index
(IOS used in this post was 12.4(9)T1 with Cisco 3745 router.)
More info:
http://www.cisco.com/en/US/tech/tk583/tk617/technologies_tech_note09186a00800949e2.shtml
No comments:
Post a Comment