One of the key portion of that advanced product is SSL VPN. It used to be called in the past Web VPN. It is usefull in the situations where you need to reach network resources in your company LAN from remote location. Most likely it will be home, cofee shop etc. In this post we will focus on how to access your computer at work from home using Remote Desktop, OWA (Outlook Web Access) and internal website with News and Anouncements, it can be even Sharepoint site.
Take a look at the logical diagram:

As you can see we have 2 Routers. One of them for your remote location (R2) and one of them (R1) at our company site. R2 does not have to be cisco router, it just has to provide internet connection. The network between R1 and R2 (172.16.0.0/16) acts as an internet in this lab environment. In this lab both routers are Cisco 3745 with IOS C3745-ADVIPSERVICESK9-M 12.4 (9) T1.
The configuration can be done via SDM (GUI software to configure Cisco Devices) or CLI.
R2 config:
R2#show run
Building configuration...
Current configuration : 935 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R2
!
boot-start-marker
boot-end-marker
!
enable secret s
!
no aaa new-model
!
resource policy
!
memory-size iomem 5
ip cef
!
interface FastEthernet0/0
ip address 10.0.0.2 255.0.0.0
ip nat inside
ip virtual-reassembly
duplex auto
speed auto
!
interface FastEthernet0/1
ip address 172.16.0.2 255.255.0.0
ip nat outside
ip virtual-reassembly
duplex auto
speed auto
!
!
!
ip http server
no ip http secure-server
ip nat inside source list 10 interface FastEthernet0/1 overload
!
access-list 10 permit 10.0.0.0 0.255.255.255
!
control-plane
!
alias exec s show ip inter brief
!
line con 0
exec-timeout 0 0
logging synchronous
line aux 0
line vty 0 4
password v
login
!
!
end
Below is a R1 config:
Current configuration : 3841 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R1
!
boot-start-marker
boot-end-marker
!
logging buffered 51200 warnings
enable secret s
!
aaa new-model
!
!
aaa authentication login default local
aaa authentication login sdm_vpn_xauth_ml_1 local
aaa authorization exec default local
!
aaa session-id common
!
resource policy
!
memory-size iomem 5
ip cef
!
!
crypto pki trustpoint TP-self-signed-998521732
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-998521732
revocation-check none
rsakeypair TP-self-signed-998521732
!
!
crypto pki certificate chain TP-self-signed-998521732
certificate self-signed 01
!---- output cut ---
ED20B032 D4BDEF14 5A114136 4C9F1794 3C3AA01E E670BC18 FC19B9B5
quit
username cisc0 privilege 15 password 0 cisc0
!
!
!
!
!
!
!
interface FastEthernet0/0
ip address 192.168.0.1 255.255.255.0
ip nat inside
ip virtual-reassembly
duplex auto
speed auto
!
interface FastEthernet0/1
ip address 172.16.0.1 255.255.0.0
ip nat outside
ip virtual-reassembly
duplex auto
speed auto
!
!
!
ip http server
ip http authentication local
ip http secure-server
ip nat inside source list 10 interface FastEthernet0/1 overload
!
access-list 10 permit 192.168.0.0 0.0.0.255
!
!
!
!
!
!
control-plane
!
!
!
!
!
!
!
!
!
!
alias exec s show ip inter brief
!
line con 0
exec-timeout 0 0
logging synchronous
line aux 0
line vty 0 4
password v
transport input telnet ssh
!
!
webvpn gateway gateway_1
ip address 172.16.0.1 port 443
http-redirect port 80
ssl trustpoint TP-self-signed-998521732
inservice
!
webvpn context First
title-color #FFFF00
secondary-color white
text-color black
ssl authenticate verify all
!
url-list "First"
heading "Web Sites"
url-text "OWA" url-value "http://192.168.0.10/owa/exchange"
url-text "News" url-value "http://192.168.0.10/news"
!
port-forward "portforward_list_1"
local-port 3000 remote-server "192.168.0.100" remote-port 3389 description "XP1 RD"
local-port 3001 remote-server "192.168.0.10" remote-port description "DC1 Remote Desktop"
!
policy group policy_1
url-list "First"
port-forward "portforward_list_1"
default-group-policy policy_1
aaa authentication list sdm_vpn_xauth_ml_1
gateway gateway_1 domain mydomain
inservice
!
!
end
If you accomplish that config on the XP2 you can connect using web browser. After you login you need to Start Application access. The Java applet will create a VPN and using IP 127.0.0.1:3000 you will be able to connect to your computer at work while being at home!
Login screen from XP2:
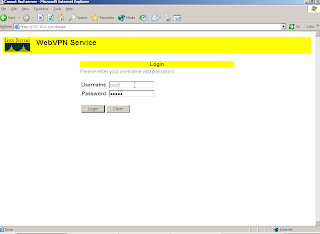
After you login and click Start Application Access you will see: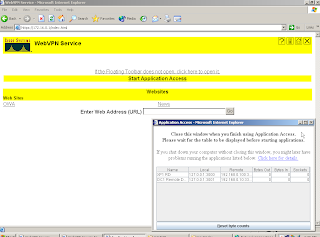
More info:
http://www.cisco.com/en/US/products/ps6496/products_configuration_example09186a008072aa61.shtml
http://www.cisco.com/en/US/products/ps6496/products_configuration_example09186a008071c58b.shtml
![Reblog this post [with Zemanta]](http://img.zemanta.com/reblog_e.png?x-id=2102b30c-dfa6-4138-9df9-741b5d325efd)
No comments:
Post a Comment